Inventing simple electronic voting for Wikimedia Estonia general assembly
How we conducted a reasonably secret ballot using our digital equivalents of collecting hats and ballot papers and thereby maintained control and trancparency of the democratic process.
For general assembly of Wikimedia Estonia we quickly built up a secret ballot system for online elections simple as putting your ballots in a hat and counting them in front of everybody interested. It wasn’t only that it felt right, but it might be that cryptographically advanced voting systems, besides many of them being expensive to use, also disconnect us from basic understanding of the democratic process. In following I describe how we found another way, building on existing practises in Wikipedia communities and how to generalize from this experience.
Wikipedians certainly are a peculiar tribe, used to collaboratively editing encyclopedia articles in plain text and presenting themselves under pseudonyms while doing that. It is also from years of experience that they have learned not to mess things up while doing that. Voting doesn’t happen that often on Wikipedia, but when it does, it makes use of the same collaborative pseudonymous editing. So it was only natural when we realized, that because of COVID-19 pandemic we cannot physically hold our general assembly, we started thinking of how we could make use of our existing practises to do it online.
What we ended up with
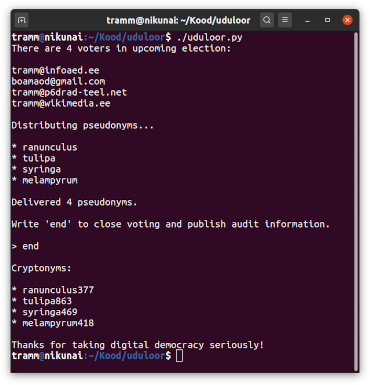
Beside the text here you see our proud voting commission member Ivo Kruusamägi giving instructions to Wikimedia Estonia general assembly. He is running a Wikimedia Meet video conference on a computer at his left hand and on a computer at his right hand he has just executed a simple Python 100-liner to deliver voting credentials to members present at our digital assembly. He is a veteran Wikipedian, but does not really have any experience in Python or coding.
He instructs our members to go and check their mailboxes to see if each of them has received an e-mail containing a pseudonym which was just randomly assigned to each member. Couple of minutes before he was editing the very same Python script, where he inserted e-mails of all our members eligible to vote.
The script is called Uduloor, which is Estonian for “Veil of Mist”. Sole purpose of this beginner level piece of program code is to select random words from the list of flower names and send each member one of those. This was basically all we needed to conduct transparent and auditable secret election on our public Internet.
Equipped with a pseudonym, each member went to a designated page at a collaborative text editor Etherpad, which is yet another public service Wikimedia Foundation hosts besides the encylopedia. Into this public text file every member wrote down a pseudonym just received, followed by the names of preferred candidates for Wikimedia Estonia board. You can see it happening in a video clip beside the text as well as in the original Etherpad replay.
The process took about 20 minutes during early afternoon of 13th of June 2020, which was the day our assembly was held. This is about the same time that it takes for an experienced volunteer to conduct an equivalent election at the physical assembly, which we could not have because of the ruptures of the first COVID-19 wave.
Was it a real election?
Yes, absolutely! In scientific literature this type of electronic voting is categorized as “elections with a public bulletin board”. The idea of providing not only procedural, but also direct digital transparency of the ballot box in electronic elections is older than the Internet. However, the cryptographic models for ensuring secrecy of the ballot and the integrity of bulletin board are still actively debated.
Besides the technological component every election is also a social convention, where the parties involved agree on a method to reach a joint decision. Discussion about high end cryptographic assurances is guaranteed to leave most of the participants as well as the organizers clueless. Relying on common technologies that people already have some practical understanding of can have an advantage in following the election and building trust in the process.
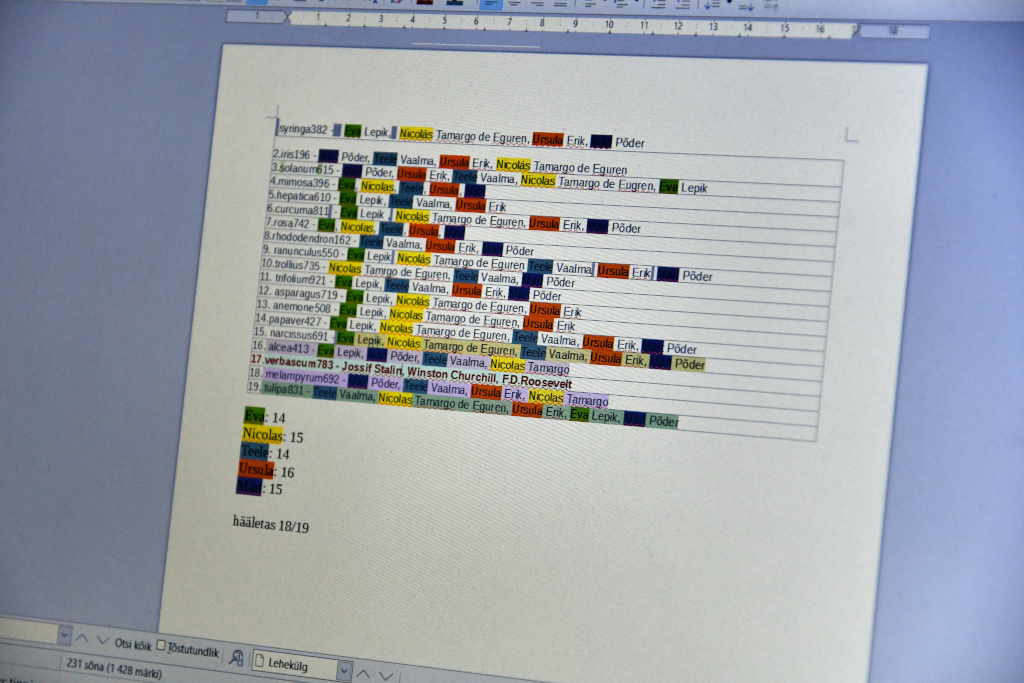
Let us inspect the editing history of our bulletin board in some detail.
First thing is that one of voters uses a pseudonym which initially looks like solanum15, but is changed to solanum615 just before the end of vote. This happened because looking at incoming votes someone noticed a discrepancy and shouted in our video conference, that probably this pseudonym has a fatal typo. All other pseudonyms had codes appended with three digits, but this had only two. The voter heard that and went to fix the mistake. It couldn’t be fixed by anybody else, because only the voter had an e-mail declaring the full and correct form of the pseudonym.
Second thing is that you see a voter with a pseudonym verbascum783 preferring Big Three leaders of WWII as members for our board. This is actually an invalid ballot, but not because of the content. The pseudonym itself is not in the list of eligible voters and this vote was discarded in the tally. Besides delivering flower names with appended three-digit random numbers our beginner level Python script did one more thing. It published the full list of delivered pseudonyms after the end of vote.
Finalizing the results
Our voting commission had the responsibility to check if the pseudonyms used at our public bulletin board were the ones actually sent to voters. We couldn’t do it during our 20 minute voting session, because we didn’t know what pseudonyms were delivered.
Our Python powered “Veil of Mist” held this information only at its runtime memory and printed it out as its last task just before exiting at the end of vote. Also the information about which voter received exactly which pseudonym was irreversibly lost after the program terminated, or maybe even earlier, because of Python interpreters memory management at its internal garbage collecting processes.
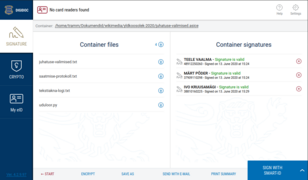
As a voting commission we finalized the results by digitally signing our Python 100-liner in its final form and the output it produced, our interpretation of the results based on votes cast on a public bulletin board, but also the full logs of video conference that was used to conduct the assembly. We included this in our official report to court register, which approved our election and updated the the list of board members in the official registry.
Certified by an invalid ballot
As suggested above, every election is also a social convention. This has a huge part in our case, because we opted for having full control of the democratic process by organizing election ourselves, using our digital equivalents of collecting hats and ballot papers.
If we used an external tool for the vote, there might have been questions and controversies about the process which we couldn’t possibly answer. Instead we chose to use common everyday tehnologies, thereby knowing exactly the amount of ballots delivered, how they were delivered and what could be the reason for someone not having received a pseudonym. Or what browser settings to modify, if access to Etherpad bulletin board service happens to be restricted. In practise we had to instruct voters to check their spam folders and in the end everybody found their pseydonyms as well as their way to the bulletin board.
Overall the two deviations from the process observed on the bulletin board instead of disproving the vote had rather the opposite effect. They assured that this election as well as every election is a common democratic endeavor, that we are all part of and that the result is the fruit of a common effort.
And it certainly gave election commission an actual job and a meaningful responsibility.
Some preliminary analysis
But does it really make sense at all instead, for example, placing your trust in Ben Adida’s cryptographically excellent heliosvoting.org, choose to trust your own sticks and stones process? Already several times I have referred positive implications of maintaining control of the democratic process.
In our basic trust model, we chose to bet on the institutional independence of Google SMTP service for delivering our pseudonymous ballot papers and Wikimedia Foundation hosted Etherpad to collect them. Until the presumption of independence and disinterest of those parties holds, our election is rather safe from malicious interventions. But we would most certainly lose our intended democratic control, if the amount of voters or interest of influencial parties grows too large.
It might also be that we were able to hold an election that way because of already existing practises in Wikipedia communities. Two out of three prerequisites for this kind of process are arguably proficiency in collaborative text editing and positive acknowledgement of using pseudonyms for community polls. In any other community, these might have been contested before even advancing to third and maybe not so obvious requirement, which would be basic code literacy.
It’s not that Wikipedians are coders though and in our discussion the proposal to deliver pseudonyms by using a Python script came from Teele Vaalma, not a coder, but another veteran Wikipedian. Editors of Wikipedia arguably manifest higher code literacy as well as trust in code than most of other common tribes, because years of experience in editing Wikitext markup, making use of templates, Wikidata queries and other scripting tools while maintaining the encyclopedia.
If you inspect the way we delivered pseudonyms, maybe it wasn’t really needed to print them during delivery. We mostly did it in order to give election commission some first hand assurance about what was sent out. In order to guarantee that the commission itself can not maliciously intervene in the bulletin board, for example inserting votes in the name of abstaining voters, we instructed our Python code to salt each pseudonym with three appended random numbers and thereby rendering them into “cryptonyms”.
Popularizing pseudonymous voting?
Although this is probably one of the simplest ways to hold a secret ballot on the Internet, the complexity quicky grows if you start adding features to the process. But even the basic part of delivering the pseudonymous ballot papers using a Python script is not approachable for most of people.
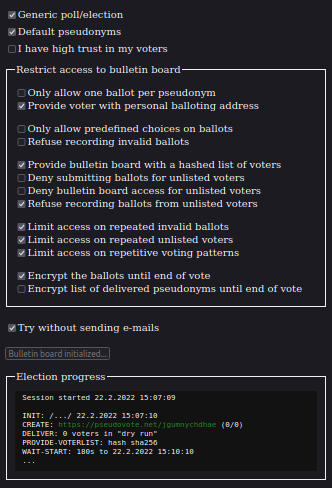
Inspired from our experience, I created a simple web service to try out the process of pseudonymous voting as we conducted it Wikimedia Estonia. Initially it was meant for our members to better follow and understand the process, but recently I decided to develop it into a test site for trying out different properties this kind of pseudonymous voting with a public bulletin board can have.
Althogh it mimics our actual voting process, this is primarily meant to be used as a tool for voter education. If you really like the idea of using pseudonyms for secret ballot and want to try it out in your organisation, then using this web service as an independent bulletin board for collecting the votes could be an option.
However, if you think about using the same service for delivering the pseudonyms AND collecting the votes, you either want to trust me with a responsibility I really don’t want to take or are probably still a bit confused about the basic concepts of electronic voting. It’s nothing wrong in being confused, but in this case using this web service in a real election is no more than first sign of willing to take digital democracy seriously.
Concluding remarks
In discussions about electronic voting the topic is too easily switched to generic requirements of IT security, which is usually yet another way of disconnecting voters from democratic process. And to ensure that election follows democratic principles is quite different goal than just building a secure IT system. You can’t really render elections trustworthy and democratic by just adding more elements from the generic cyber security toolbox.
There is a famous decision by the Consitutional Court of Germany which states that in a democracy, election is a public process and in case of using electronic voting in a real election “it must be possible for the citizen to check the essential steps in the election act and in the ascertainment of the results reliably and without special expert knowledge”.
The real life example above should be considered as an experiment and an effort to follow “the principle of the public nature of elections” in practise. Being rather uninteresting from cryptographical and IT security point of view, in the environment of current acceptance and transparency levels of technology this is probably the closest you can get to the public auditability of electronic voting.
Quoting Josh Benaloh’s doctoral dissertation from 1987 on using public bulletin boards and homomorphic cryptography for auditable electronic voting:
Fortunately, the mathematics in this schema is, although somewhat detailed, accessible at the undergraduate level or even conceivably the high school level. If an election schema such as this were to be adopted for large-scale use, it could be accompanied by an effort to educate people about the mechanism involved. A short undergraduate mathematics course or even an advanced high school course should be sufficient for this purpose.
Maybe enabling our students and people in our organisations to have first hand experience with even the most simplest forms of secret ballot in electronic voting would be the first step in common acceptance of more advanced election cryptography?
This is an updated and extended version of an earlier write-up from 2020 in the blog of Wikimedia Estonia. The processes described are to be considered in the context of Non-profit Associations Act of Estonia, which in its current from quite contradictingly does not regulate secret ballot in real time electronic assemblies, but explicitly forbids it in other forms of electronic assemblies. Wider context of electronic voting in Estonia might be relevant, but is out of scope of this report and is part of my yet to be published project on e-voting in Estonia.