What's (still) wrong with Estonian e-voting?
Estonia spouts official and binding electronic elections since 2005 and it has been a controversial yet an interesting journey. The building blocks of initial system have been replaced, but the lure of trusting operational security instead of democratic oversight is still very much there.
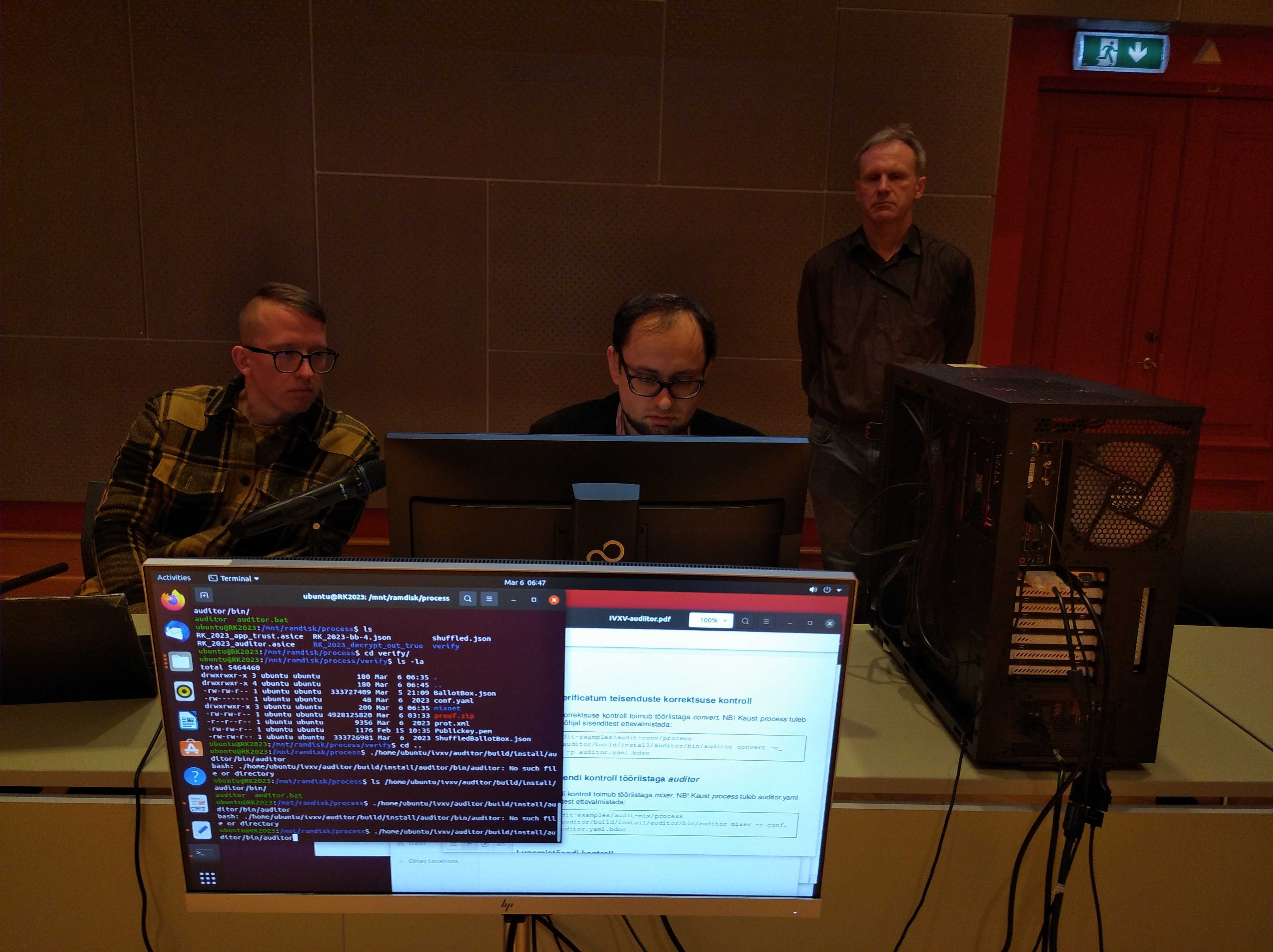
This is my initial and somewhat edited report as an observer of e-voting in 2023 parliamentary elections in Estonia. Procedures are far from over yet, because several complaints have been filed, at least one of them having included this report as evidence. But even without all the aftermath it really has been interesting. You don’t get to write an independent tool for vote verification and generating voter cryptograms using command line tools every election. Maybe something interesting will come of it, but it will probably take time. I’ve been paying attention to what is happening to e-voting in Estonia now about 10 years and if there will be any changes, they will be slow, but appear unexpected.
WARNING! This is an initial “needs assessment” part of the full report called “Votes without ballots: e‑voting at 2023 elections in Estonia”. The full report with the explanations to general public as well as retrospective analysis was presented at Chaos Communication Congress in 2023 (see summary and slides) and at the plenary of the Estonian Parlament in 2024 (see press release and the full transcript).
Twenty years of history
Estonian e-voting started from two academic reports from cryptographers and computer scientists in 2001, that resulted from political discovery of this innovative and appealing concept. In April the cryptographers proposed a six year plan to get to first official e-voting, described verifiability standards for individual votes, universal verification of the tally and predicted the inevitability of voting on Internet in next 20 years. In October the computer scientists gave a somewhat more encouraging report, although stating the need for long term plan they were positive of getting to first iteration already in couple of years. At the same time they stressed the social dimension of the project, need for using only open source software, vote collection by multiple independent authorities and introductionary restrictions to voting at unmonitored environments, like homes.
What happened next is that cryptographers were dubbed idealists from ivory tower of academic Tartu and completely dismissed, the computer scientists were recognized for their effort of describing double envelope system for digital votes, but majority of their precautions still dismissed, and 2003 resulted in a white paper which proposed to build e-voting using simple public key cryptography and extra attention to operational security. This resulted in test run early 2005 in Tallinn and already first binding e-voting during 2005 municipal elections. The invention was mostly praised high by digitally minded younger generations, but president Arnold Rüütel disputed the constitutionality in supreme court and mayor of Tallinn, Centre Party leader Edgar Savisaar also backed away stating concerns about democratic rights.
After that population has been polarized to the extreme by e-voting, however Centre Party quickly stopped complaining after getting into government in 2016.
There have been two major changes to the system and both of them have been rather forced. First of them resulted from a software introduced by a history student Paavo Pihelgas in 2011, which demonstrated how malware can stop votes from reaching the collection service or even change the content of the ballot. As a result OSCE observation mission suggested creating a verification mechanism for individual votes which was introduced in 2013. Verification mechanism allowed voters to get a confirmation of received ballot in collection service up to 30 minutes after voting and even see the content of submitted ballot.
The infamous report by J Alex Halderman and his team just before 2014 European Parliament elections didn’t have a immediate policy impact, but rather helped to fortify the story of the rest of the world not understanding our advanced digital society. Professor Halderman and his team presented their findings as observers of 2013 municipal elections and following lab experiments demonstrating client and server side attacks, suggesting e-voting should be discontinued because of “fundamental architectural problems that cannot be resolved with quick fixes or interim steps”.
The second major change happened after 2015 elections where I happened to become a poster boy of at that time anti e-voting Centre Party, because by reverse engineering official voting application I casted an invalid ballot and made a public fuss about not knowing whether it will be counted or what will happen. I used the public attention to write an opinion piece in major newspaper referring to initial reports by Tartu cryptographers and clamoring for more verifiability and less blind trust. This resulted in introducing a new cryptographic scheme in 2017 with homomorphic encryption, shuffling of the ballots by mixnets and a tally with zero knowledge proofs. Although still in 2019 usage of those tools was largely faked and votes still decrypted into plain text during the first tally without any mixing to get quick results, besides supreme court nobody really noticed, but apparently the system has been actually used in elections after my complaints.
The curse of operational security
The major problem of Estonian e-voting system is that because of historical reasons the two verification mechanisms are not linked together. In academic literature there is a concept of “end to end verifiability” which suggests that voters and public should have means to make sure of the vote is correct even when the voting commission is fraudulent or the server software malfunctioning. This is achieved by giving voters and auditors tools independent from election commission and other government institutions to check whether the votes are cast, stored and counted without any tampering. The concept is widely acknowledged in academia, but also e-voting projects in Norway and Switzerland took it as a core requirement. Switzerland has even written into federal law that nation wide elections have to embrace cryptographic means that provide “complete verifiability”. This is the popularized form of this scientific term which usually consists of individual and universal verifiability.
Despite its own two components of verifiability, Estonian e-voting still heavily depends on operational security. The individual verifiability component covers verification only up to 30 minutes of casting the individual vote, which means that voter can only make sure the collection service has received the vote, but has no means of independently making sure that the vote was also included in the final batch, that was counted. There is a gap between individual verification of casting the vote and universal verification of the tally, which can mean that the vote is without independent oversight up to a week, if voter gives her vote immediately when e-voting starts. This is not end to end verifiability in a sense recognized by the academic literature and rest of the world. There is some verifiability on both ends indeed, but it’s not from one end to another end – it doesn’t make the ends meet.
The operational security is also heavily relied on during vote counting processes that take place after the polling stations are closed on Sunday. Although at some point the ballots will be anonymised and shuffled into mixnets, there are still procedures to remove ballots of voters who did cast their ballots on paper that override the e-vote. There is also a procedure to remove multiple votes from the same voter, keeping only the one with the latest timestamp. There are also some other changes in voting rights that are taken into account removing yet another batch of votes from the final tally, that is to be sent into mixing and counted. Those procedures rely on operational security and in voting handbook they are even not specifically checked by data auditor – the concept that was introduced in 2017 to give e-voting some touch of auditability and reduce reliance on blind trust in operational security.
So I would say that we still have a long way to go to get to the system that was proposed by Tartu idealists already in 2001 and is now mostly recognized by the rest of the world. There was a government commission on e-voting that was gathered in 2019 that proposed 25 changes to improve the situation. I was part of that commission and I basically went there to do one job – add the requirement of end to end verifiablity to the list. This materialized as a proposal 25 of the list. The company that is currently the data auditor at the elections was hired in 2022 to compose another report about that 25 item todo list. Although it says that everything is in perfect order and the recommendations are progressing, I have seen none of it, neither from department of technical protocol nor legal changes or clarifications which were anticipated by supreme court in 2019.
In an ideal situation we would have individual vote verification that would be available up to the moment when the votes are tallied or maybe even longer instead of 30 minutes after casting the vote, a change that was also implied by proposal 11 of that commission. It is a technical matter of how to bind together the individual verification and universal verification, but we won’t have true observability and auditability of e-voting until they don’t meet or even better somewhat overlap. Of course there is much more into the processes, observers etc, but this is a fundamental issue with Estonian e-voting – it is still collection of separate hacks without proper perspective to the whole. And on top of that there is still no analysis of the constitutionality of e-voting, that presidents and mayors were complaining about. Supreme court has only made couple of minor observations and suggestions during discussions of various election complaints – usually they are referred to as analysis of the constitutionality of e-voting, which they are not.
My interventions in 2023

Although I have a sporadic habit of running in elections myself, mostly to support certain movements or just to learn new things, this year I have been free from that kind of responsibilities. This is why I took time to join local election observers team, where I already made a hassle complaining about the computer system, where the master keys for election were generated. According to election manual the process is audited and the observers as well as the auditors need to have means to make sure that the key generation system doesn’t contain malware. It would be really devastating if the fundamental component for the rest of the e-voting process would be compromised and malware could manipulate the key generation or even leak the private key. The same system is reused to count the votes on electon day, so it’s really a crucial link in the chain.
Although the voting operators first went to completely ignore my proposal to make an image of the hard disk used in the process, during next day I repeated my proposal and asked for clarifications about ignoring my request for comments. The answer was the usual operational security one about that visually observing that the disk is there and sealed after use is enough to make sure it doesn’t contain malware. But for most of people who know anything about computers this is complete nonsense. Even in our home computers we run software to detect malware, so how come visual observation suffices for this system that is used to generate master keys for the whole election?
After the official complaint the commision discussed the topic with me and agreed that I should at least be able to take a look into something, to have any kind of assurance about the system being malware free. So they offered me that I could inspect the disk image that was used to create the hard disk used in key generation. I kind of agreed with the idea of taking a look at it, but I also made an inquiry about how they will prove that the image they provide me with was actually used to create the disk. I suppose even from viewpoint of operational security that kind of procedure has to be somehow registered, checksums written down etc. I am still waiting for the answer to that question and although I was promised to get to inspect the disk image immediately after counting of votes, this was postponed to next week, also leaving my questions about the details of their proposal unanswered.
Independent vote verification tool
But as a much more interesting side project I also took my time to create individual vote verification tool independently from official tool that comes as a smartphone application. I opted to make it a Python 200 liner, which besides checking the vote gives the voter a possibility to download the actual digitally signed cryptogram, decrypt it and keep it for whatever later use. This is interesting because the official tool hides most of the process from voters and has lead people to false sense of security. After 10 years of individual vote verification, the election commission still has not managed to inform the public, that QR code used for verification actually discloses your full vote with your digital signature. This is very hard evidence about the vote and unwanted disclosure certainly undermines secrecy of the ballot.
The first public cameo of my tool happened to be someone wanting to use it for downloading and decrypting the QR code of the vote by president Alar Karis, who was shown to cast his electronic vote on national broadcasting prime time news – and at the same time exposing his QR code. Hopefully the QR code was already expired for the time vigilant citizen arrived – but we can only guess. Next day the journalists from Geenius Meedia went for a journalistic experiment to see if the QR code can be actually read from news clip and proved that this is the case and the vote of the president could have really leaked. If noone from our public broadcaster and from president’s team has learned that QR code is leaking your vote, what then about common voters? Something is really adrift here.

According my observations Estonia despite its endeavor for being a digital pioneer has a certain aversion for privacy rights, for example being one of the EU countries implementing GDPR after final deadline and having problems with it’s enforcement. High level proponents of e-voting, among them current chancellor of justice have been telling that maybe we even need to get rid of principle of the secrecy of the ballot as we have known it.
I find it highly problematic though and I wonder if people just don’t know about the implications about the technological protocol of our e-voting. I doubt that president actually wanted to leak his vote. E-voting as a topic tends to be so extremely polarized that even IT professionals instead of checking up the protocol get into fights about if the system is cool or not just like that – for example my post referring to my article in national broadcaster’s news portal about vote verification tool was immediately removed from one of the oldest discussion groups for IT professionals. The reason appeared to be that it sounded like being against e-voting for administrators who happen to be from extreme pro e-voting crowd. This is just the latest example, and a very mild one, but echoes the widespread denial of problems with e-voting among Estonian IT circles that has been in permanent red zone after the visit of professor Halderman’s team.
Independent voting application
Since e-voting system in Estonia is not tested by general public of hackers and professionals as in some other countries, there are not so many efforts to come up with independent tools for voting. There is a rather extravagant single-board voting machine project by one of the creators of e-voting protocol though. The whole e-voting system is complicated enough to install on your own server because it takes a lot of configuration. Without an actual server it is cumbersome to test your software and even the the creator of the protocol failed to correctly cast his vote with his independent voting machine during 2021 elections.
This is why my independent tool was very much anticipated among people paying attention to advancements in e-voting and it really has the qualities of exemplifying the protocol and educating voters about how things actually happen in the system. I feel that this is very important for the future of e-voting and as one of my hobby projects I have created an educational yet functional voting machine to be used for teaching basic concepts of e-voting to kids. It still needs polishing to render it into actual learning object with teacher’s guides etc, but I think we need to have kids using, modifying and manipulating voting software as part of civic education programs and programming classes. That is, if we actually want to have meaningful future for e-voting in Estonia or elsewhere.
Compared to vote verification tool the voting application is a complex piece of software involving steps like digitally signing your vote and encrypting the ballot. Digital signatures are a paid service, that you cannot encapsulate into Python code for everybody to run just like that.
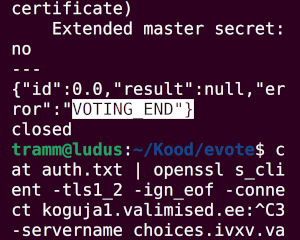
During two last days of e-voting I experimented with the idea of creating a dedicated bash script and come up with the mixture of tools needed to cast the digital vote. I was successful to the rate of 2021 independent voting machine – I was able to cast a vote, but in the end I was in a so big hurry that I didn’t have time to properly format it. So it will probably end up as yet another invalid vote in the system. But what also happened during my experiments with the protocol is that when I got the VOTING_END message from the server at 20:00, I was still able to submit a vote couple of minutes after by accident. It will be interesting to see how this will be sorted out, because I wasn’t using the official voting application which probably was built to guide the process somehow and for my after hours vote there will be probably some discussion how to handle that.
Messing with the ballot box
The question about what is in the ballot box and what is not is really intimately bound to the dilemmas of operational security. Also the biggest public scandal of 2023 e-voting is arguably some people being provided the wrong candidate lists in the beginning of the vote. This could have been solved by public announcement that they have to revote or their votes will be counted as invalid ballots in counting phase. It seems self evident, but instead the voting commission chose to remove the ballots from the ballot box. This is probably something that should be avoided at all cost and is just utterly wrong, because voting commission deliberately removing or adding ballots is the bona fide voters worst nightmare.
But it also contradicts the whole logic of secret ballot and idea of double envelope system that is meant to convey that. In fact they were removing ballots they couldn’t even inspect, because the ballots in their envelopes are in encrypted form. So they could actually contain correct votes, despite what the commission presumes. This has resulted in a complaint to Supreme Court by Sulev Švilponis, which has a really strong constitutional basis. The court usually dismisses such complaints arguing that observers can only file complaints about violation of their own individual rights, but this is about illegal counting process leading to incorrect results. Ingoring this would be very much against the common sense of justice.
The practical question here for me as a voter submitting series of votes by means of homebrew voting application is about the actual status of my own ballot, or rather ballots, leading to the same inherent and recurring dilemmas. First of all, was my vote counted? If it was, how do I know which vote was counted, if I submitted series of correct and incorrect ballots, but for all of them I received positive answer? We are back at my 2015 situation of having submitted a Schrödinger’s vote.
Since they have not removed any votes that were submitted after deadline, they could say they accepted my last vote. During recount they said they removed test votes cast too early, so shouldn’t they remove votes cast too late? I don’t really have an excuse for submitting the vote after deadline. So maybe they will count the vote I submitted 19:59? That might be so, but if they couldn’t actually decrypt the ballot, which actually seems to be the case, is it a vote at all or just a random array of bytes? Maybe they should skip this communication and consider it as a failed attempt to cast a ballot, which it in fact was and rewind to vote that was successfully decrypted and condisder this my actual choice at the elections? In fact they deny the right to cast invalid ballots, so why would they want to declare my communication invalid ballot, if they have a correct one available?
This is why status of my after hours vote is very interesting. There have to be very strict rules about removing votes from ballot box as well as accepting them into ballot box. We can’t be thinking of a reason for removing individual ballots from physical ballot box, because without any doubt this would be manipulation of the vote – whatever might be reason we give. Should it be different for the digital ballot boxes of e-voting? If it really should, shouldn’t we be able to observe the process and to ensure that these kinds of things are not done to manipulate the results? With all those open questions I ended up filing my own complaint to Supreme Court demanding my vote to be counted according to the law and not the vote processing software, which implements its own divergent procedures.
There seem to be no good answers to these questions in the operational security framework, where the trust is delegated to security team and not to strict rules based on proper legal acts or mathematical infallibility of a cryptographic protocol. However, these are the questions that definitely arise and there really is a point in actually discussing the constitutional requirements of e-voting and moving on with the issue as proposed by Indrek Teder, our previous chancellor of justice, and which current chancellor of justice Ülle Madise agreed to do in 2016 and later, but failed to investigate in 2019, when I provided her with an opportunity.
Technology is not neutral
Although the long time project lead and author of 2003 white paper has left the team, the legacy of operational security is still very profound in the technical circles around e-voting. Yet in time it has rendered into being hectical, although there is a mantra of always telling the public that everything is perfect, never mind the operational messups following the e-voting from election to election and the diminishing attention given to procedures. I think this was done better in last generation of e-voting, or at least they were able to leave an impression. For example, there were public sessions for preparing hardware for the processes where observers could make sure official sources were used to install operating system and other software, thereby indeed minimising the risk of malware in the system. For critical procedures they even claimed to use random computers bought from the market to avoid manipulations by insiders. At least that’s what they told the observers and the journalists. Although current handbook of e-voting repeats optimistic statements from older versions, historical procedures that used to form their basis scrapped they are devoid of all meaning now.
The operational security presumptions for e-voting are contradictory, because they express promises they can’t fulfill. That’s why the accompanying rhetoric occasionally takes really weird forms. One of the ever emerging motives is that if we hardened the verification standards, it will lead to vote selling and voter coercion. They say it’s because voters should not be able to prove who they voted for. But this doesn’t make sense if our existing system leaks digitally signed votes in the form of cryptograms, which is hardest digital evidence of the vote that you could think of. OSCE observation mission pointed at this problematic in their 2019 report saying that you shouldn’t be able to easily break ballot secrecy even after the election and probably not even for invalid ballots. In their 2011 report where they suggested individual vote verification, they also proposed that it should be done using a code known only to voter and not by disclosing digitally signed votes in full.
Of course we know everything better in our digital wonderland, but it still is rather hard to debate the fact, that our current system in its technical implementation and its proponents quite openly challenge the common concept of vote secrecy, which in fact is the main guarantee against voter coercion. The fact that the voters don’t understand the technical protocol and don’t know that their QR codes are disclosing their votes doesn’t mean they actually like the idea. Probably they just don’t understand. The rationale of our electoral agenda seems to be not helping them to understand or to protect their privacy, but to gaslight them into giving it away altogether. Trying to convince us that this is being done to stop voter coercion is almost devilish. But the whole affair certainly exemplifies the need to understand the system at the protocol level, because this is what creates our voting experience and builds up into our election principles.
Black market for voter cryptograms
As an example of to what extent our current system enables voter coercion and vote selling is to think about using cryptograms and other data sources in conjunction. This is probably what would it be in practise, when malicious vote buyer appears. Using different data sources together can make the voters really able to prove their vote with almost 100 per cent certainty.
We are told that recasting the vote after coercion is proper means to retain voting freedom, but this is only partially true, if perpetrator can demand proof that voter did not cast another electronic ballot after the deal. There is a service called MyID, which is a side product of our digital identity infrastructure. We have had it for ages and MyID is the new one currently in beta. Each electronic vote is signed digitally and for giving a digital signature the software has to check if the certificate used for signing is a valid one. The service logs all the attempts to digitally sign a document and provides logs with timestamps, IP addresses, type of identification token and other data. If the log doesn’t contain a certificate check for another digital signature with the same properties as the previous one, but later timestamp, this is the proof needed to make a deal. You can also download full logs in convenient JSON format to be analysed and processed or even order it sent directly to perpetrators e-mail, which simplifies the process to a large extent.
Luckily from 2021 the law was changed to make paper ballot vote on the election day to override the electronic vote. This seems to be a good instrument against coercion, but the voter lists circulated in polling stations are treated as common personal data, which is processed by many people during and after the elections. It is not very hard to obtain this data, especially for certain polling stations or regions. This creates another possibility of hardening the deals, because from these records one can make sure that voter didn’t override e-vote with paper ballot. Although focusing too much on voter coercion we are probably a bit misguided about the motivations of participants of these kinds of deals – probably both parties are interested in making the deal happen and to keep it secret. There are numerous ways for the voter to prove the content of the vote if there is a will to sell and an interested buyer.
But there is even more to it, because according to 2023 statements by election commission you can just send a digitally signed request to info@valimised.ee and ask for confirmation of which type of vote was counted in election. Initially they promised to disclose even more data, but reconsidered during the process of answering data requests. It is still unclear if they can deny such requests under GDPR article 20, if there is no proper legal basis for such a refusal. I was personally awarded a private vote counting session to inspect my votes after my persistant attempts to get to the data. I wasn’t allowed to record any video or take pictures of the data, so I had to memorise checksums and timestamps involved to compare it with the data I already had from MyID service and resulting from downloading QR codes and cryptograms.
This is weird at all levels. Their initial plan would have obsoleted all the previous attempts to secure the process against voters being able to prove who they voted for, but still their procedures are rather superficial and certainly not protecting us from black market of votes, if we have other means to obtain the same data. Paradoxiclly the election commission does not want voters to be able to cryptographically verify that the commission actually stores the vote not only up to 30 minutes, but also days after the ballot was submitted, stating that this would make voters to be able to prove their vote. Yet their processes leak the same information, although you need to use the old fashioned e-mail communication and combine it with personal data requests. Or do they actually consider their proofs not being able to prove that ballot that was actually counted?
It’s beyond my understanding what is the actual rationale of electoral commission by doing all this, but here I summarised it to explain how much the current protocol pushes us to sacrifice our privacy and how that has eventually become part of current practises. If you nourish that kind of system, some variety of the implications become true, for example you cannot really protect people from accidentally showing their QR codes or electoral commission eventually starting to share the information they collect and people have right to access, although it undermines voting privacy. Maybe it’s worth pondering on if that’s actually the direction we want to take with our rather young democracy – maybe learn from Switzerland instead, that measures its democratic tradition in centuries rather than decades?
Protocols and code are the law
Estonia is a small country and smaller communities can have a really specific take on privacy, because basically everybody knows everybody and you just have to live with the fact. And we have a rather special e-voting protocol which has properties of vigorously defending operational security instead of layman observability and verification plus creating a political space where vote secrecy and privacy are rendered really fragile. Do you know that Estonia is the only known country that publishes lists of all members of political parties? This is not by accident or because of a leak, but a requirement of the law, that might well be part of this special Estonian take on privacy and democracy. But is it actually a good thing?
It might be that twenty year long defense of operational security and mimicking the acknowledged concepts of verifiability is just something that happened, but usually people do things for a reason. I haven’t noticed dark web services offering amounts of bitcoin for my cryptograms yet and until now there have been no major fluctuations of opinion polls versus voting results, that might get people thinking that there is massive election fraud happening.
But it is not that protocol and code are just neutral things. They talk and they talk a lot about what will be the reality around us if we fail to pay attention to the technical details. Currently they talk quietly and take precedence over our laws which are rather tailored to fit the technical system than vice versa. This is hardly a good democratic practise, but it’s hard to measure exactly how bad it is. In current form the protocol leaves open the possibility of manipulating the system in the worst possible way. How can we be sure? Estonian society is quite digital all right, but at the same time this advanced digital society fails in being conscious about itself.
It appears that my report has been included as evidence in election complaint to Supreme Court, which based decision on my 2019 complaint argues that since requirements for electronic voting are still not properly stipulated by law, the act of determining the election results has been illegal. I have personally filed another complaint about Schrödinger’s vote situation to Supreme Court and provided an expert opinion on ballot secrecy issues to law firm challenging the results of e-voting in Supreme Court. Probably there will be follow-ups, but I will post them as separate posts and refrain from editing this report except for spelling mistakes or updating the links.